Training & Support
To ensure a smooth transition and effective use of the new system, we provide comprehensive training and ongoing support services.
1. Training Sessions
- User Training: Conduct training sessions for end-users to familiarize them with the system’s features and functionalities. Training will include hands-on exercises and practical examples.
- Administrator Training: Provide specialized training for system administrators covering system configuration, user management, and maintenance tasks.
- Training Materials: Supply detailed training materials, including user manuals, quick reference guides, and video tutorials.
- 2 training sessions is provided.
- Subsequent training sessions will be $400 per session only.
Note: Time limit of maximum 3 hrs. per session
2. Post-Deployment Support
Help Desk Support: WhatsApp + SLA, email
Service Level Agreement (SLA)
Working Hours: Our support team is available Monday to Friday, from 9:00 AM to 6:00 PM.
- Ticket Acknowledgement: All tickets will be acknowledged within 2 hours of submission during working hours.
- Issue Resolution:
- Minor Issues: These include non-critical problems that do not significantly impact the system’s performance. Resolution time is within 2 hours of acknowledgement.
- Major Issues: These include significant problems that affect critical functionalities but do not completely halt operations. Resolution time is within 8 hours of acknowledgement.
- Critical Issues: These include severe problems that cause system downtime or major disruptions requiring code changes. Resolution time is within 24 hours of acknowledgement.
Change Request
Process
To ensure that any changes in the project scope are managed effectively, we will implement a structured change request process. This process will help in assessing the impact of changes on the project timeline, cost, and resources. Estimated man day for change request is 700-900 SGD. The steps involved in the change request process are as follows:
- Initiation: A change request is initiated by the client or project team.
- Documentation: The change request is documented, detailing the nature and reason for the change.
- Impact Analysis: The project team conducts an impact analysis to assess the effect of the change on the project scope, timeline, and cost.
- Approval: The change request, along with the impact analysis, is submitted to the project sponsor for approval.
- Implementation: Upon approval, the change is implemented by the project team.
- Review and Closure: The change implementation is reviewed, and the change request is closed after ensuring that the change has been successfully integrated into the project.
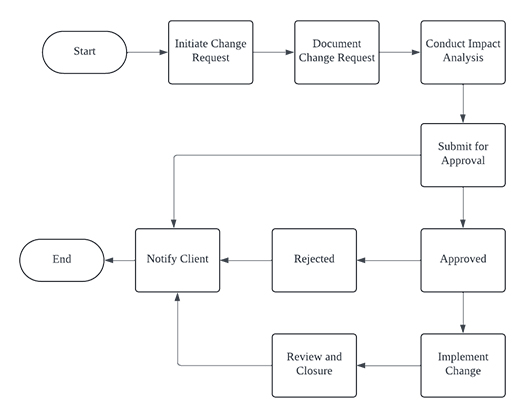
Change Request Table
| Step |
Description |
Responsible Party |
| Initiate Change Request |
A change request is initiated by the client or project team. |
Client/Project Team |
| Document Change Request |
The change request is documented, detailing the nature and reason for the change. |
Project Manager |
| Conduct Impact Analysis |
The project team conducts an impact analysis to assess the effect of the change. |
Project Team |
| Submit for Approval |
The change request and impact analysis are submitted for approval. |
Project Manager |
| Approved |
If approved, the change is implemented by the project team. |
Project Sponsor |
| Implement Change |
The approved change is implemented. |
Project Team |
| Review and Closure |
The implementation is reviewed, and the change request is closed. |
Project Manager |
| Rejected |
If rejected, the client is notified. |
Project Manager |
| Notify Client |
The client is notified of the approval or rejection. |
Project Manager |
Acceptance Criteria
Acceptance criteria define the conditions that must be met for the client to accept each deliverable. These criteria ensure that the deliverables meet the agreed-upon requirements and quality standards.
1. Functional Requirements
- Feature Completion: All specified features and functionalities must be implemented and operational.
- Performance Standards: The system must meet the performance standards outlined in the requirements
2. Non-Functional Requirements
- Usability: The system must be user-friendly and intuitive for end-users.
- Security: The system must adhere to security standards and protect against unauthorized access and data breaches.
- Compatibility: The system must be compatible with the specified hardware and software environments.
3. Documentation
- User Manuals: Comprehensive user manuals must be provided, detailing the system’s features and functionalities.
4. User Acceptance Testing (UAT)
- UAT Completion: The client must complete UAT and provide formal acceptance of the system.
- Feedback Implementation: Any feedback or changes requested during UAT must be addressed and verified by the client.
5. Deployment and Training
- Successful Deployment: The system must be successfully deployed in the production environment.
- Training Completion: Training sessions for end-users and administrators must be completed, and training materials must be provided.
Communication Plan
Effective communication is crucial to the success of any project. Our communication plan ensures that all stakeholders are informed, engaged, and aligned throughout the project lifecycle. The plan includes the following components:
*Support Business Hours: Monday to Friday 9am to 6pm
1. Regular Meetings
- Kick-off Meeting: An initial meeting to introduce the project team, outline project objectives, and discuss the project plan.
- Weekly Status Meetings: Held every week to discuss progress, address any issues, and plan for the upcoming week. These meetings will include the project manager, key team members, and client representatives.
- Ad-hoc Meetings: Additional meetings as needed to address urgent issues or significant changes.
2. Status Reports
- Every Two Weeks Status Report: Detailed reports summarizing weekly progress, including completed tasks, upcoming tasks, issues, risks, and any change requests.
- Final Project Report: A summary of the entire project, including successes, challenges, and lessons learned.
3. Points of Contact
- Project Manager: The primary point of contact for all project-related inquiries and communication. Responsible for coordinating meetings, distributing reports, and ensuring effective communication among all stakeholders.
- Client Representative: Designated by the client to facilitate communication from the client’s side, provide timely feedback, and participate in decision-making processes.
Training
Genic Solutions Pte Ltd shall provide technical support staff with on-site training to operate, maintain, and effectively utilize each module of the B2B Platform in the course of their daily activities. The training shall primarily follow a train-the-trainer model and appropriately precedes the Implementation Schedule noted above. Primary users include both clerical and professional staff with varied levels of technical experience.
Comprehensive and quality training and support are critical to the success of this project. Each employee participating in training shall receive an abbreviated instruction booklet for desktop use and instruction on the use of the product manual(s) or online help. Training shall be by group and if deemed necessary by the client, on an individual basis. Follow-up training is on an as-needed, as-requested basis.
There will be two training sessions provided by Genic Solutions. A subsequent training session will be quoted accordingly depending on a remote training or physical training basis.
Data migration
1. Client Data Preparation:
- The client is responsible for providing all existing data that needs to be migrated to the new system. This data must be sanitized and formatted correctly according to the specifications and templates provided by the vendor.
- Ensuring the accuracy and completeness of the data is crucial. The client must verify that all data is accurate, up-to-date, and free from any errors or inconsistencies before submission.
2. Data Migration Assistance:
- Once the client has provided the sanitized and correctly formatted data, the vendor will assist in migrating this data to the new system. The vendor will work closely with the client to ensure a smooth and efficient migration process.
- The vendor will conduct initial tests to verify the integrity of the migrated data and ensure that it aligns with the new system’s requirements.
3. Migration Timeline and Support:
- The timeline for the data migration process will be established based on the volume and complexity of the data provided. The vendor will provide a detailed schedule and regular updates throughout the migration process.
- The vendor’s support team will be available to address any issues or concerns that may arise during the data migration. The vendor is committed to ensuring a seamless transition to the new system.
4. Compliance and Data Security:
- During the migration process, the vendor adheres to strict data security protocols to protect the integrity and confidentiality of the client’s data.
- The vendor complies with all relevant data protection regulations and industry best practices to ensure the secure handling and transfer of data.
By adhering to the above procedures, the vendor aims to facilitate a successful data migration, ensuring that all client data is accurately and securely transferred to the new system.
Data Encryption
1. Database Encryption:
- All data stored within our system, including personal details and sensitive information, will be encrypted using industry-standard encryption protocols. This ensures that all data is protected both at rest and in transit.
- We utilize AES-128-ECB (Advanced Encryption Standard with 128-bit keys in Electronic Codebook mode) OpenSSL encryption for database encryption. This method provides a strong level of security to safeguard your data against unauthorized access.
- Our encryption strategy complies with relevant data protection regulations and industry best practices to ensure the highest level of security for your data.
2. Password Encryption:
- Passwords will be hashed using the SHA-256 algorithm. This hashing method ensures that passwords are stored securely and are resistant to brute-force attacks.
- The SHA-256 hash function is part of the SHA-2 family of cryptographic hash functions designed by the National Security Agency (NSA) and is widely recognized for its security and reliability.
3. Encryption Management:
- We implement strict access controls to ensure that only authorized personnel have access to encryption keys and sensitive data.
- Regular audits and security assessments will be conducted to ensure compliance with our encryption policies and to address any potential vulnerabilities.
4. Compliance and Best Practices:
- Our encryption methods adhere to international standards and regulatory requirements, including GDPR, HIPAA, and other applicable data protection laws.
- We continuously monitor and update our encryption protocols to align with evolving security standards and technological advancements.
Two Factor Authentication (2FA)
1. 2FA for Login:
- To enhance the security of user accounts, we implement Two-Factor Authentication (2FA) for all login processes. This additional layer of security requires users to verify their identity using two different methods before gaining access to their accounts.
2. Email OTP as 2FA:
- As part of our 2FA implementation, we use Email One-Time Password (OTP) as a secondary verification method. Upon entering their password, users will receive a unique OTP sent to their registered email address, which must be entered to complete the login process.
- This ensures that even if a password is compromised, unauthorized access is still prevented without access to the user’s email account.
By incorporating robust encryption methods, including AES-128-ECB OpenSSL for database encryption, and Two-Factor Authentication, we aim to protect your data from unauthorized access and ensure its confidentiality and integrity.
Personal Information
By using our Services, you acknowledge that Genic Solutions will process your personal information as described in our Privacy Statement. You confirm that:
- You have provided appropriate notice and obtained all consents for us to process personal information.
- If you are providing personal information of third parties, you have obtained the required legal permissions.
- If there is any conflict between this Agreement and our Privacy Statement, the Privacy Statement will prevail.
Copyright Ownership of Intellectual Property
- The Vendor, Genic Solutions Pte Ltd, shall retain full ownership of all source code, software, designs, and related materials developed under this agreement, regardless of the payment status by the Client.
- Upon receipt of full payment, the Vendor grants the Client a non-exclusive, perpetual license to use the software for its internal business purposes. The Client shall not have any rights to modify, distribute, or otherwise exploit the source code or software beyond the terms explicitly agreed upon in writing by the Vendor.
- The Vendor reserves all copyright and intellectual property rights unless otherwise agreed upon in a separate written agreement.
Your Rights to use the Services
License Grant
The Services are protected by copyright, trade secret, and other intellectual property laws. You are only granted the right to use the Services and only for the purposes described by Genic Solutions within this Agreement. Genic Solutions reserves all other rights in the Services. Until termination of this Agreement and as long as you meet any applicable payment obligations and comply with this Agreement, Genic Solutions grants to you a personal, limited, nonexclusive, non-transferable, non-sublicensable, revocable right and license to use the Services.
Restrictions
You agree not to use, nor permit any third party to use, the Services in a manner that violates any applicable law, regulation, or this Agreement. You agree you will not:
- Provide access to or give any part of the Services to any third party.
- Reproduce, modify, copy, sell, trade, lease, rent, or resell the Services.
- Decompile, disassemble, or reverse engineer the Services.
- Make the Services available on any file-sharing or application hosting service.
- Create a database in electronic or structured manual form by systematically downloading and storing all or any of the Services.
Content and Use of the Services
Responsibility for Content
Content includes any data, text, graphics, images, videos, software, or other materials made available through the Services. By making your content available through the Services, you grant Genic Solutions a worldwide, royalty-free, non-exclusive license to host and use your Content.
Restricted Use
You shall not use the Services for:
- Illegal, fraudulent, defamatory, obscene, pornographic, or abusive content.
- Impersonation, identity fraud, or misleading representations.
- Spam, chain letters, pyramid schemes, or malicious software.
- Unauthorized data scraping, hacking, or security breaches.
Genic Solutions reserves the right to suspend or terminate your access for any violations.
Payment
For Services offered on a payment or subscription basis, the following terms apply, unless Genic Solutions or its third-party affiliate notifies you otherwise in writing.
- Payments will be billed in Singapore Dollars (SGD) plus applicable taxes (including GST) as per product ordering and subscription terms.
- Payment methods include:
- Cheque in favour of “Genic Solutions Pte Ltd”
- Online transfer to the bank account of “Genic Solutions Pte Ltd” (mentioned on the invoice).
- If your payment and registration information is not accurate or updated, Genic Solutions may suspend or terminate your account.
- Genic Solutions may use recurring billing programs to update your payment information to avoid service interruption.
- Services will be automatically renewed annually at the then-current rates unless cancelled per the Agreement. Client can cancel the renewal services with one month notice period without any obligations.
Additional Items
No Professional Advice
Genic Solutions does not provide legal, financial, accounting, tax, healthcare, or real estate advice. Consult a professional if needed.
Communications
Genic Solutions may send important service updates via email or post on our website.
Account Security
You are responsible for managing your password securely and must notify Genic Solutions of any unauthorized access.
Disclaimer of Warranties
Your use of the Services is at your own risk. Genic Solutions provides the Services “as is” and does not guarantee:
- Suitability for a particular purpose.
- Security, bug-free experience, or uninterrupted access.
- Compliance with legal requirements.
To the maximum extent permitted by law, Genic Solutions and its affiliates disclaim all warranties.
Content and Use of the Services
Responsibility for Content
Content includes any data, text, graphics, images, videos, software, or other materials made available through the Services. By making your content available through the Services, you grant Genic Solutions a worldwide, royalty-free, non-exclusive license to host and use your Content.
Restricted Use
You shall not use the Services for:
- Illegal, fraudulent, defamatory, obscene, pornographic, or abusive content.
- Impersonation, identity fraud, or misleading representations.
- Spam, chain letters, pyramid schemes, or malicious software.
- Unauthorized data scraping, hacking, or security breaches.
Genic Solutions reserves the right to suspend or terminate your access for any violations.
Data Storage
Data is to be stored in the AWS server of Genic Solutions. Client can always export the data from the system with the help of excel exports.
- Data Ownership: The Customer retains full ownership of all data stored on AWS server. Genic Solutions does not claim any rights to this data. Only Source code belongs to Genic Solutions .
- Security Measures: The Customer is responsible for implementing and maintaining robust
security measures, including encryption, firewalls, and access controls, to protect stored
data from unauthorized access. ( in case of local. For Cloud it will be under AWS with Genic Solutions )
- Access Control: Only authorized personnel, as determined by the Customer, may access the data. The Customer must manage access rights and ensure they are regularly reviewed and updated.
- Data Backup and Recovery: The Customer must establish and maintain regular data backup and recovery processes to prevent data loss and ensure business continuity. Genic Solutions also keep the backup services with AWS for contingency plan. Data backup is retained for 15 days. ( Genic Solutions responsibility in case of AWS)
- Compliance: The Customer is responsible for ensuring that data storage and processing
comply with all applicable laws and regulations, such as GDPR, HIPAA, and local data
protection laws. ( Genic Solutions responsibility in case of AWS)
- Confidentiality: The Customer must maintain the confidentiality of stored data and
implement measures to prevent unauthorized disclosure. ( Genic Solutions responsibility in case of AWS)
- Breach Notification: In the event of a data breach, the Customer must notify the service
provider and affected parties within 48 hours of discovery. ( Genic Solutions responsibility in case of AWS)
- Liability: The service provider is not liable for any data breaches or security incidents
resulting from the Customer’s failure to maintain adequate security measures.
Privacy Policy
As a company, protecting the privacy and data security of our clients’ customers are of the utmost importance. To that end, Genic Solutions have established the following privacy and data security policy:
Data Collection:
Genic Solutions collect only the minimum amount of data necessary to provide our services to our clients. Genic Solutions do not collect any personal information without explicit consent.
Data Use: Genic Solutions uses clients’ data only for the purpose of providing the services requested by our clients. Genic Solutions do not use this data for any other purpose, nor do Genic Solutions shares this data with any third parties.
Data Security: Genic Solutions takes all reasonable measures to protect the security of our clients’ customers’ data, including:
Encryption: All data is encrypted both at rest and in transit.
Access Control: Access to data is restricted to only those employees who require access to perform their job duties.
Physical Security: Our servers are hosted in secure facilities with 24/7 monitoring and surveillance.
Regular Audits: Genic Solutions regularly audit our systems and processes to ensure compliance with industry standards and best practices.
Data Retention: Genic Solutions retains clients’ customers’ data only for as long as necessary to provide the services requested by our clients, or as required by law.
Data Deletion: Genic Solutions deletes clients’ customers’ data upon request, subject to any legal obligations Genic Solutions may have to retain certain data.
Data Breach Notification: In the event of a data breach that may affect our clients ‘customers’ data, Genic Solutions will notify clients immediately and provide any necessary assistance to minimize the impact of the breach.
Compliance: Genic Solutions comply with all applicable privacy and data security laws, regulations, and industry standards. By adhering to these policies, Genic Solutions aims to protect the privacy and data security of our clients’ customers and maintain their trust in our services.
Export restrictions
The Services are subject to Singapore export laws. You agree not to export or re-export the Services in violation of applicable laws.
Language
The English version of this Agreement prevails over any translated versions.
General terms
This Agreement constitutes the entire agreement between you and Genic Solutions . Any invalid sections will be removed without affecting the remainder of the Agreement.
- You cannot transfer this Agreement without Genic Solutions ’s written approval.
- Genic Solutions may transfer this Agreement to an affiliate or successor entity without your consent.
Terms of Agreement
Non-Disclosure
Both parties agree to keep this information confidential. No parties will be allowed to disclose directly or indirectly the content of this agreement to any parties without written approval from either party.
Feedback & Revision
The client could request to send feedback to Genic Solutions within 4 days of receiving the quotation. If the client does not respond within the stipulated timeframe, the feedback will be marked as accepted. Up to 2 revisions from the customer side are accepted after signing off, on the document. If there are errors in the quote, then it will be Genic Solutions ’s responsibility. That will not be counted as a revision.
Limited Liability
In no event shall Genic Solutions be responsible for any consequential, special, punitive, or other damages, including, without limitation, lost revenue or profits, in any way arising out of or related to any of the services fulfilled as per the endorsed Quotation. Genic Solutions shall have no liability for any failure or delay resulting from any governmental action, fire, flood, insurrection, earthquake, power failure, riot, explosion, embargo, strikes whether legal or illegal, labor or material shortage, transportation interruption of any kind, work slowdown or any other condition beyond the control of Genic Solutions , affecting production or delivery in any manner. You agree to indemnify Genic Solutions against any claims arising from your misuse of the Services.
Changes to the Agreement
Genic Solutions reserves the right to modify this Agreement at any time. Changes will be effective when posted on our website or notified through the Services.
Termination of Agreement
If Work is postponed or canceled at the request of the Client, Genic Solutions shall have the right to bill pro rata for work completed through the date of that request. The pro rata rate will be $550 daily for design work and $650 daily for technical work and is subjected to a Minimum Cancellation fee of 50% of the Total Contract Value. Any notice of cancellation must be provided in writing. If at the time of the request for termination, work has been completed beyond the amount covered by the initial payment, the Client shall be liable to pay for all work completed at the hourly rate stated above or the full payment.
Cancellation of PO/Quotation Proposal acceptance is not allowed. A cancellation fee will be charged at 50% of the total quotation amount.
Genic Solutions recognizes the Client’s financial protocols and would in this case start this project once the client has signed this contract. There will be no cancellation of the contract once it is signed by the client. Client can cancel the renewals of services anytime with one month of notice.
Governing law & jurisdiction
This Agreement shall be governed by the laws of the Republic of Singapore. Any disputes will be resolved in Singapore courts.
